Hello there, Carders! In this article, I am aiming to share how to bypass KYC. I will go a head and show you how i succeeded in bypassing the KYC utilized by financial apps and small scale banks utilizing real-time deepfake and how these apps can relieve or diminish this risk.
Important Notes
Note: For these cardable sites, you don't need OTP bots if you're using a non-VBV card. Non-VBV cards bypass 2FA automatically. But don't worry—if you accidentally choose a VBV card, we've got you covered with the ultimate OTP bots tutorials to help you bypass 2FA with ease.

Disclaimer:
I am not capable in the event that some person employments this data in this web journal against someone, and I have composed the article fair to spread mindfulness among those app devs and individuals who utilize those applications.
Read: Learn carding from beginner level to pro strictly for free
Let’s begun with article on how to bypass KYC!
To begin with of all, I have made a deep fake by utilizing one real-time profound fake site; I am not attending to share that site, but you folks can discover it online. I utilized that site to swap my confront with Elon Musk’s confront, at that point I recorded a video of facial movements and took a picture of the same.

I would then require an application or web application that allows me to upload a video or selfie image for KYC verification in order to test my proposal. I discovered that this was being done via a microbanking app on my phone. I discovered the API being used for verification after reverse-engineering the application. Then, instead of testing the banking application, I choose to open a test account with the API provider and test the API provider directly. I observed that this API verifies the identity through face feature recognition and liveness detection. In essence, nevertheless, a person can simply fool with his visual identity if he avoids liveness detection. Test result 1: Successfully avoiding passive liveness detection
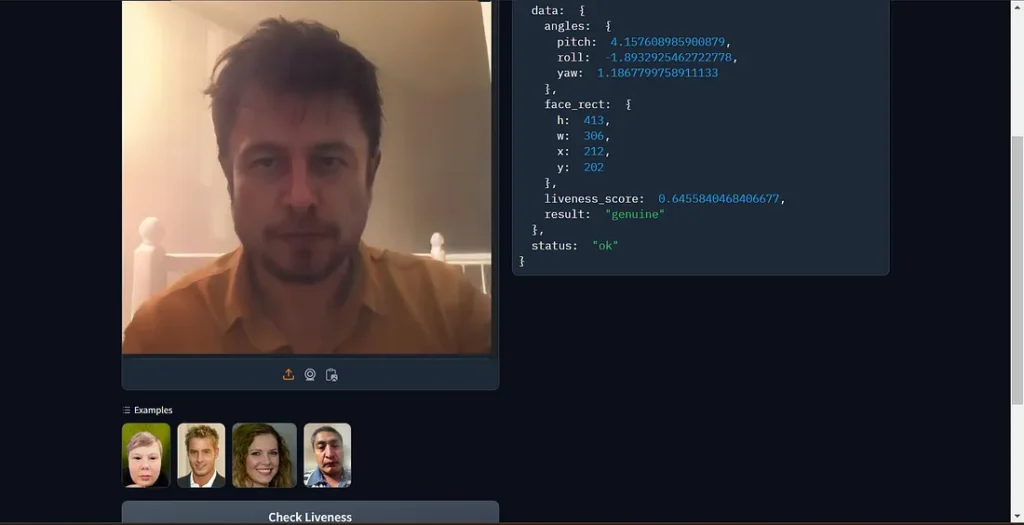
I tested another API with similar functionality and successfully bypassed passive liveness detection (Test result 2).
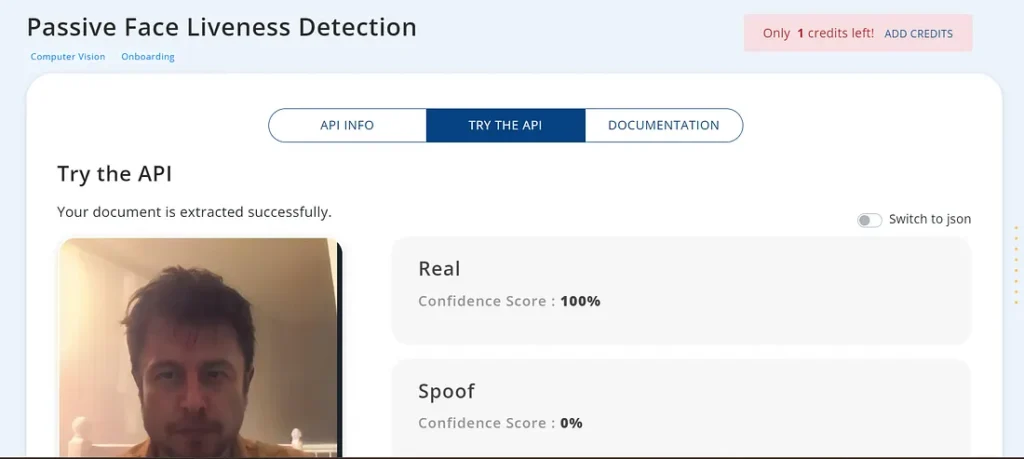
I tested another API with similar features, but it failed to bypass passive liveness detection (Test result 3).
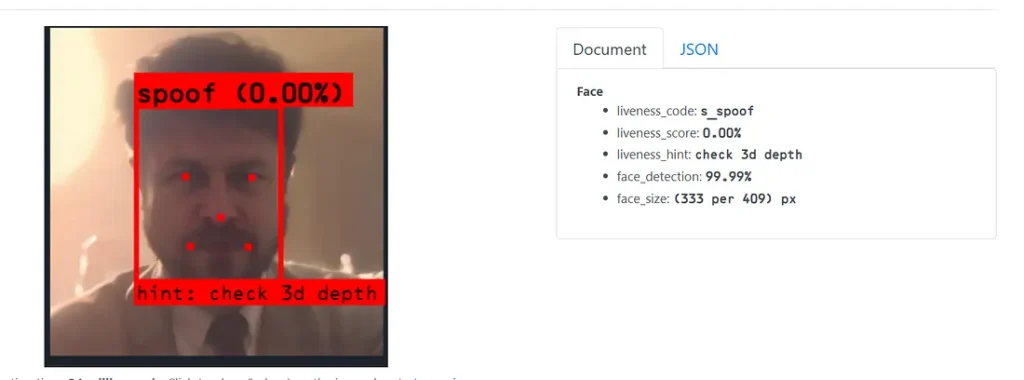
I also learnt that certain websites utilise deepfake detection with liveness detection, therefore I tested those websites with my custom-made deepfake image and video.
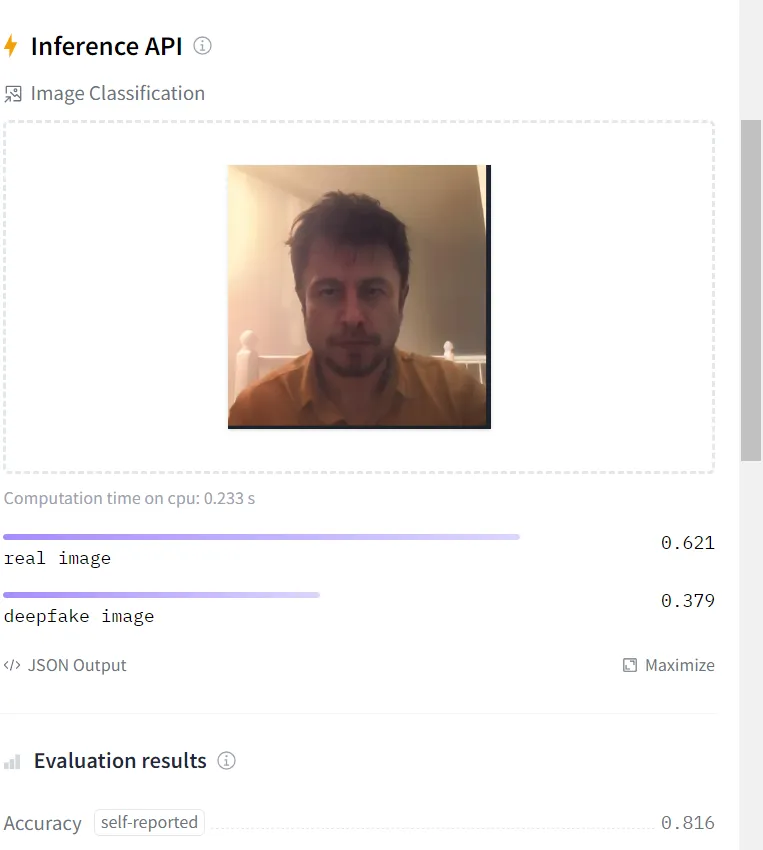
Test result 1 — Successfully bypassed deepfake detection
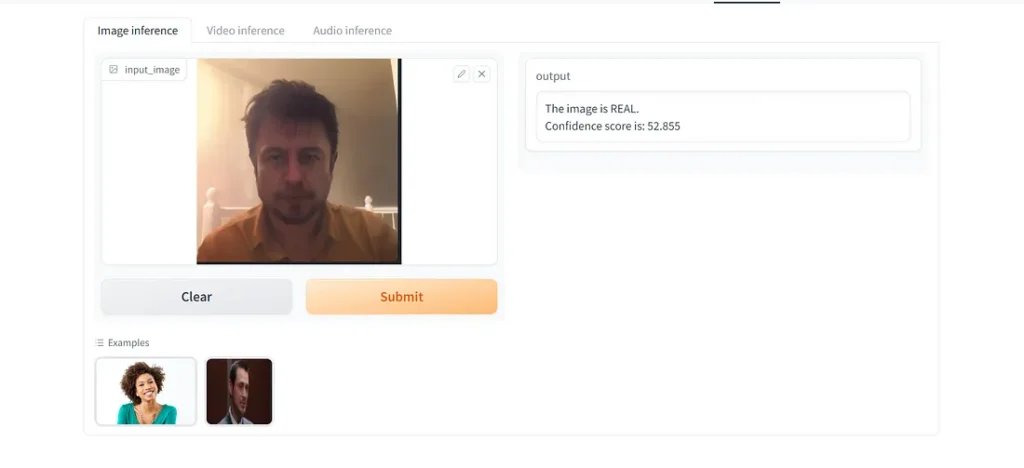
Test result 2— Successfully bypassed deepfake detection (Bypass KYC)
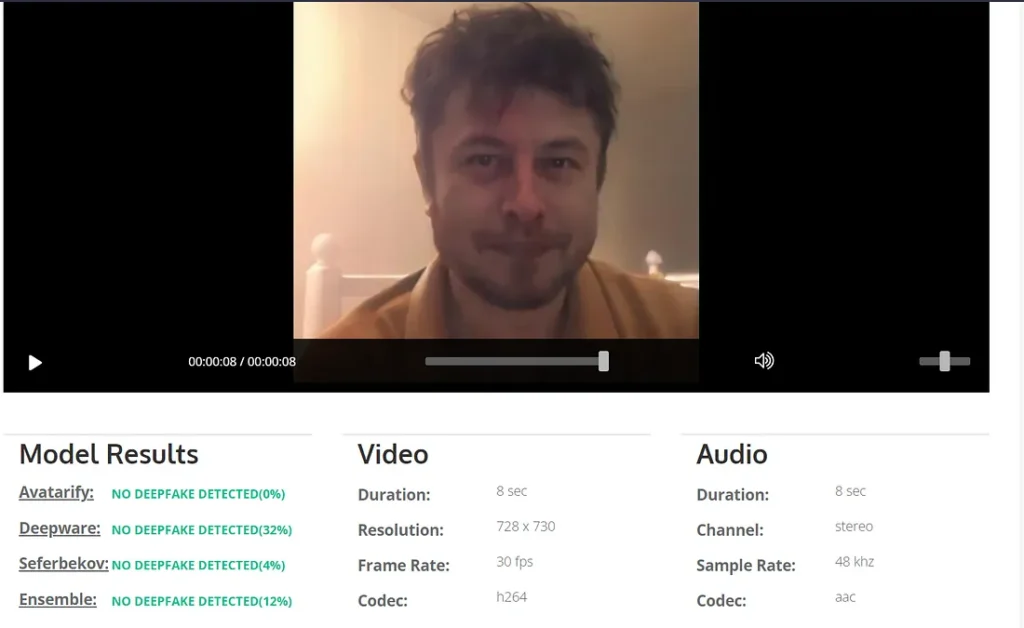
Test result 3: Successfully avoided deepfake detection.
From the previous experiment, we can see that I was able to overcome several lifeness detection and deepfake detection APIs used in several applications. Let us try to uncover the root cause of those issues.
The majority of liveness detectors and deepfake detectors use classifier algorithms. When detecting deepfakes, we should reduce bias in the classifier model and use multiple facial features and signals to detect fraud in the applications.
Based on our experiments, we can conclude that 3D liveness detections work better than 2D liveness detection. In addition to facial authentication, I should use some type of second factor authentication.
Steps to secure application against deepfake
To detect deepfakes, we should reduce bias in the classifier model and use multiple facial features and signals to detect fraud in the applications.
I should confirm with facial authentication and some sort of two-factor authentication as well.
Legal and policy measures: Create explicit policies and legal frameworks for the production and distribution of deepfakes. This can include user agreements that ban your program from being used to create or propagate deepfakes. Promote a community approach in which users can report suspected deepfakes. This not only aids in rapid detection but also improves community awareness.
Collaboration with Other Entities: To keep ahead of deepfake technologies, work with other corporations, academic institutions, and government agencies. Collaboration can help to develop more effective detection and prevention techniques.
Regular Monitoring and Updates: Keep an eye out for new forms of deepfakes and update your detection systems as needed. Deepfake technology is always changing, so staying up to date is critical.
User Verification: For applications where identity is critical, conduct rigorous user verification, including biometric verification, to confirm that users are who they claim to be.
Transparency and Reporting: Be upfront in your efforts to combat deepfakes; report any identified deepfakes to the appropriate authorities. This will help to establish trust and a sense of responsibility. Thank you for reading my essay.
SECURING CONNECTION...
Zero to $10,000: The 7 Secret Easy Cashout Glitch!

-
Instant Bank Glitch›
-
New Cash App Glitch›
-
Secure Paypal Glitch›
⚠️ URGENT: $4,200 Daily Cashout Glitch is LIVE.



















Leave a comment